Year after year, billions of dollars continue to be lost from phishing attacks, as threat actors continue to evolve. Today, the most popular strategy used by threat actors is spoofing. A spoofing attack occurs when a number belonging to an enterprise or individual is used as part of the threat actor’s scheme. It allows them to more successfully impersonate the enterprise, since their calls appear to come from a phone number belonging to the enterprise. These spoofing attacks are extremely effective because of the sophisticated use of social engineering techniques to trick people into believing they were communicating with someone each victim believes to be known and credible.
What is Spoofing: how does it happen and where is the impact?
Spoofing is surprisingly easy to get away with. When a phone call is made, part of putting that call on the phone network includes providing the number that is originating the call. The threat actors simply plug in the number they want to spoof as their caller id. Really, that’s it. Unless the carriers they use have sophisticated checks to make sure that the caller IDs are ones owned by their customers, there’s nothing in the way of the threat actor using whatever caller ID they desire.
Phone-based Threat Actors Are Omni-Channel
Threat actors evolved phishing techniques to leverage every available digital communication channel. With the rise of mobile device, new channels became available to spoof:
- Vishing: Also known as Voice Phishing, is a technique where a threat actor leaves a voice message to trick people into sharing sensitive information by pretending to be a legitimate person with a legitimate reason for communicating via voice.
- IVR Spoofing: Also known as Interactive Voice Response Phishing, is a technique where a threat actor creates a fake IVR to mimic a legitimate organization’s IVR to capture sensitive information such as passwords from victims who called what they believed to be the actual company.
- Smishing: Also known as SMS Phishing, is a technique where a threat actor leaves a text message to trick people into engaging in a text conversation and sharing sensitive information by pretending to be a legitimate person with a legitimate reason for communicating via text.
There were over 880,000 complaints in 2023 totaling in excess of $12.5 billion, with phishing a part of 34% of all complaints reported.
What is Spoofing Detection?
The Federal Communication Commission has started to combat spoofed robocalls with caller ID authentication and new regulations like STIR/SHAKEN. Carriers have further tried to use programs like branded calling to have authenticated calls look and feel different than other calls. However, even more is required to stay ahead of the threat actors across multiple channels of communication.
A successful anti-spoofing solution requires proactive monitoring of voice and SMS threats as they occur for real-time intelligence and attack detection. Successful remediation of spoofed telephony requires cooperation between carriers, consumers, and interested 3rd parties to assist with the takedown of phone-based vectors for smishing and vishing within hours of detection as well as add preventative controls along vectors in order to escalate as necessary.
One challenge is that basic fraud detection programs are limited to behavioral insights. However, with all the active participation in these programs we’ve seen, the fact remains; the only effective way to qualify the intention of the call, and accurately confirm the person calling is who they say they are, is thru content driven analytics. This approach is basically the same as what networks and email security programs use today, where they leverage the content of messages to be able to determine when fraud is happening.
Why Does It Matter?
The Federal Trade Commission also stores reports in a database called Consumer Sentinel Network (Sentinel)which is available to law enforcement. While the FTC doesn’t help with consumer cases, they do assist with the apprehension and prosecution of the perpetrators. In their 2023 Sentinel Databook they reported that losses to call/text are 284% greater than the email channel with average losses of $1,250 per case (over $1.2 billion lost to calls/text in 2023). Providers are most at risk here.
The FCC has been fining carriers $millions and shutting down flagrant violators in their “Spring Cleaning 2024” efforts to combat robocalls and spoofing. Even the FTC has gone on record to say “It’s in businesses’ best interest to consider solutions that will help protect their good name and their loyal customers.”
Improving Spoofing Detection: Protection Requires Intelligence and Disruption Services
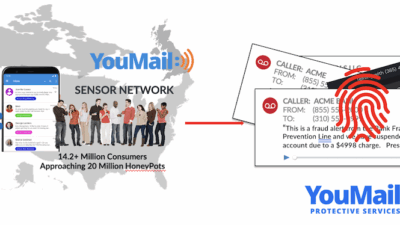
YouMail Protective Services’ managed detection and response solutions for Imposter Communications are a key tool in the fight against spoofing. These services are supported via a live threat network that collects intelligence across our million+ app subscribers (which represent all North American Mobile Networks), and in the 10s of millions of honeypots active across the US, UK and Australia.
We connect evidence to an integrated system of thousands of communication providers and enforcement agencies for intelligence, disruption, prevention & justice for direct disruptions, voice tracebacks, SMS tracebacks and network block. YouMail PS has a comprehensive program with threat briefings and self-serve dashboards for both intelligence and disruption.
Spoofing Detection for Carriers:
- Content driven analytics: get real time insights that identify the suspected illegal activity and provide actual transcripts of what your customers are saying
- Monitor your DIDs: number is being spoofed (whether it’s on your network or not), give you the call record details and the context- so you not only know that your customer’s number is being spoofed, you’ll know in what context (impersonating the customer, impersonating another enterprise, stealing the number, etc,)
- Monitor your network: call event details for suspected illegal traffic for any call transiting across your network- BYO# protection, # spoofed from upstream partner, etc.
Spoofing Detection for Banks & Enterprise
- Intel on Brand mention: real time notification with context when your brand is being impersonated (with context) across your own numbers, or any number across voice and SMS
- Detect unauthorized use & spoofing of monitored numbers with or without content
- Bi-directional API to widen view of threat data
- Identify providers & account information
– And Disruption: takedown of threat actors spoofing your number
- YouMail PS Fastlanes short-circuit accounts directly in 0-2 hours for Fastlane partners
- YouMail PS Coordinated Traceback w/ITG & CTIA in 1-7 “weekdays”, depending on hops)
- Preventative controls at participating providers
- Escalate by C&D / LEA engagement
- Intel use for direct customer education efforts
- Relay brand provided abuse reports via email or API
- Education to public by web search (Google, Bing)
- Safer Together program with device-level protection for customers/employees
Contact our sales team today to learn more about how you can get started with this essential service.